
Identity management (IdM) describes the management of individual identifiers, their authentication, authorization, and privileges/permissions, and within or across system and enterprise boundaries with the goal of increasing security and productivity while decreasing cost, downtime, and repetitive tasks.
"Identity Management" and "Access and Identity Management" (or AIM) are terms that are used interchangeably under the title of Identity Access Management, while Identity Management itself falls under the umbrella of IT Security.
RiVidium’s IdM portfolio falls in line with our Cyber Security delivery platform. We have partnered with three key titans in the field of IdM to bring to our clients the best of breed in IdM:
- Jericho Systems: EnterSpace Authorization software
- SETECS Inc.: PKI and PIV card deployment
- Microsoft Corporation: Forefront Identify Management (FIM)
A major challenge for organizations is to manage the identity of staff, business partners, and customers to control their access to resources. Because most organizations focus on managing users from an IT perspective, they tend to forget that everything attached to the network has an identity, and all identities must be protected just as if it was a human asset. RiVidium considers the management of users and resources from the perspective of mapping their identity to their interactions within/throughout the network. RiVidium addresses how users/resources gain access rights -sometimes called entitlements or permissions- and we ensure these rights are also associated with roles where they need to be.
For more information about our Identiy Management delivery platforms, please click on the tabs above.

RiVidium Inc. is a pioneer in Security and Identity Management. We have been working closely with Jericho Systems in the Identity management, protection, and provisioning space for the past 5 years.
RiVidium is a prime reseller of Jericho Systems technologies and we are the right engineers to deploy/integrate Jericho’s Identity Management solutions.
EnterSpace® Decisioning Service (ESDS) from Jericho Systems Corporation is a powerful, highly configurable software suite that supports diverse use cases, including:
- Capabilities for identity and access management (IdAM), identity management (IdM), and attribute-based access control (ABAC), including policy decision points, policy administration points, and related services.
- Securing web services (SOAP/REST), web applications, collaboration portals, and LDAP/s-enabled directories with frameworks that support widgets, plugins, and authentication services.
- Supporting physical security systems through electronic policy evaluation, policy enforcement, and event triggering.
- Detecting insider threats through audit services and compliance tracking that monitor system activity.
- Personalizing and displaying digital content dynamically customized for marketing, patient privacy, and other purposes.
EnterSpace® Decisioning Service offers these features:
- Decoupled, service-oriented architecture (SOA)
- Embeddable policy engine
- Policy administration point that can import and debug XACML policies
- Extensible audit and compliance framework that provides access to evaluation decisions and policy administration reports
- Event triggering
- Public Key Infrastructures (PKI) supporting CRLs, OCSP and SCVP
- Multi-platform support (Linux and Windows)
- Standards compliant: SAML 1.1/2.0, XACML 2.0, FIPS 140-2, SAML 2.0 Profile for XACML v2.0
- Extensible connector architecture with support for enterprise data resources including SQL, Oracle, Active Directory, and LDAP
- Federated attribute retrieval and creation of SAML-based attribute authorities
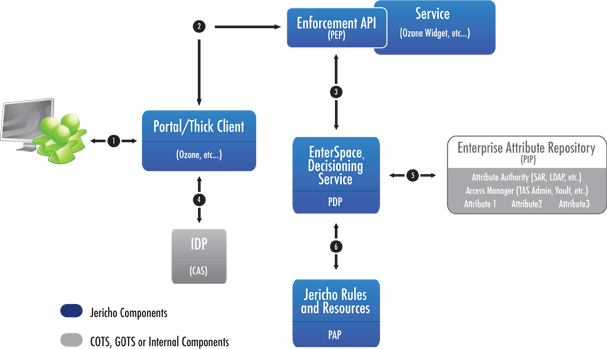
Sample EnterSpace Architecture

RiVidium Inc. is a pioneer in Security and Identity Management. We have been working closely with SETECS Inc., in the Smart Card, Personal Identification & Verification (PIV) Card, Identity management, protection and provisioning space for the past 6 years.
RiVidium is a prime reseller of SETECS technologies and we are the right engineers to deploy/integrate SETECS’ Identity Management solutions.
OneCARD™is a Cards Management System (CMS) supporting transparently multiple types of smart cards, including secret–key cryptography cards, public–key cryptography cards, file system cards, and Java smart cards. The system provides smart cards administration and multiple smart card applications (applets), it supports multiple security-enhanced applications, and it is integrated with SETECS OneMAN™ and OnePKI™ products.
Components
- Smart card administration system (issuing, updating and revocation of smart cards);
- Several internal smart card security applications based on US Government (GSA and DoD) specifications – identification/authentication, secret–key and public–key crypto;
- Smart cards platform for multiple file system cards and smart card readers, based on ISO 7816 APDUs, Javacard framework, and Open Card Framework (OCF);
- Secure applications using Java smart cards based on GSA and OCF specifications.
Distinguished Features:
- The system is based on all relevant smart card standards (ISO 7816, OCF, Javacard framework, GSA FIPS 201, DoD CAC – Common Access Card);
- The system transparently supports multiple readers and smart cards through 7816 APDUs, OCF, and GSA/DoD CAC basic smart card services interfaces;
- The system supports multiple smart card applications (secure identification and authentication, local and remote login, credit card and debit card payments, stored money transactions, loyalty and ticketing transactions, medical applications, etc);
- Integrated with OnePKI™ and OneNET™ smart card stores multiple X.509 v3 certificates.
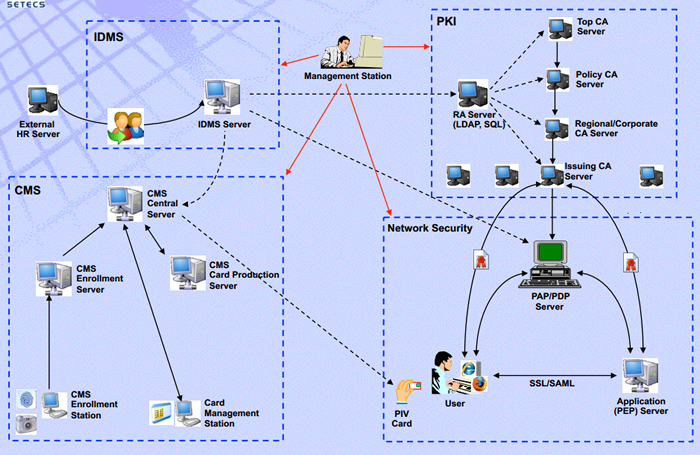
SETECS® Integrated Security Management System
RiVidium Inc. is a pioneer in Security and Identity Management. We have been working on Microsoft products, especially Identification Management & Verification for the past 8 years.
RiVidium is a prime integrator of Microsoft's Forefront Identity Manager (FIM) technologies and we are the right engineers to deploy/integrate Microsoft's FIM solution set.
Microsoft’s Forefront Identity Manager (FIM) extends the functionality of Microsoft’s Identity Lifecycle Manager (ILM) 2007 to reduce further the cost and inefficiency associated with the management of the entire identity life cycle. Building on the certificate management process, user account provisioning, and identity integration available in ILM 2007, FIM aligns the management environment to the systems and processes most appropriate to the IT professional’s or business user’s role within an organization.
Features and Benefits of FIM
FIM delivers integrated identity synchronization, comprehensive certificate and smart card management and automated user provisioning in one secure solution. The key features of FIM includes: Policy Management, Credential Management, User Management and Group Management.
Policy Management
FIM delivers a framework for identity management automation and integration so all enterprise systems run using the same set of enterprise policies. This is accomplished by:
- Centralized policy authoring, enforcement, & auditing: As part of the FIM 2010 release, we can deliver an intuitive SharePoint-based user interface that enables system architects, IT administrators, and end users to create rules governing users and groups using natural language descriptors and easy-to-use menu-driven controls. The policy management tools will also enable business owners and IT professionals to report on the events and business rules processed by FIM, and to act on that information in an automated manner. This provides a view into the state of compliance as well a mechanism to enforce business rules that support compliance.
- Extensible Windows Workflow Foundation-based workflows: FIM includes rich, visual workflow management based on the Windows Workflow Foundation, which enables IT to quickly define, automate, and enforce identity management policies. IT can use the integrated workflow in the approval / rejection process for actions such as creating accounts or delegating tasks. For further extensibility and customization, we can integrate FIM with web services APIs that enable customization at both the platform and solution levels. FIM consumes Windows Workflow Foundation (WF) workflows, enabling organizations to import and reuse existing WF-based workflows in FIM.
- Heterogeneous identity synchronization & consistency: FIM delivers integration with a broad range of network operating systems, e-mail, database, directory, application, and flat-file access. FIM supports connectors for Active Directory, Novell, Sun, IBM, Lotus Notes, Microsoft Exchange Server, Oracle databases, Microsoft SQL Server™ databases, SAP, and others. This provides organizations with the power to connect and synchronize the plethora of disparate sources of identity information in their company—in most cases without the need to install software of any kind on the target systems. Since in some cases it might be necessary to connect to custom or legacy applications unique to a specific organization, FIM extensible agent capabilities enable companies to integrate and manage identities for these applications through developing custom agents in the Microsoft Visual Studio® development environments.
Credential Management
FIM provides the ability to manage multiple credentials in an integrated manner from the administrative and end user standpoints. IT professionals will have one location where they can examine user policies, define policies, and define smart card templates and processes for resetting PINs. With FIM, the end user’s experience will be very intuitive. Credential management activities for end users will be embedded in familiar applications and integrated with familiar tools, which reduces the cost of deploying identity management for the organization and enables easier, faster adoption. To implement these goals, FIM provides:
- Credential lifecycle management integrated with provisioning: With FIM, IT professionals will be able to define policies that manage the provisioning process across user accounts and credentials. This means that workflow in FIM can be configured to automatically provision a user account, set their initial password, and initiate the process to issue the user smart cards and digital certificates. For instance, FIM can manage a user provisioning process that would not only issue a new user’s Active Directory account and set up their mailbox, but also issue the new user a one-time use pin for them to activate their smart card.
- Management of multiple credentials such as third party Certificate Authorities (CAs) and One-Time Passwords (OTPs): FIM can be extended to manage a wide range of credentials that your organization uses to secure resources. The certificate and smart card management capabilities introduced in ILM 2007 can now be extended to provide centralized management of additional strong authentication factors, including management of third party CAs and OTP devices, which includes partner solutions.
- Self-service password integrated with Windows logon: FIM enables users to change and reset their own passwords and smart card PINs from the Windows desktop login.
- Configurable authentication gates for self-service password reset: RiVidium can deploy FIM as a question-and-answer authentication gates, and includes extensibility to build additional types of gates – for instance a smart card gate or a gate that requires a user to enter a code sent to a mobile phone. The enrollment process for authentication gates is configurable, ensuring that all users in an organization enroll – for instance requiring registration at login.
- Simplified sign-on by synchronizing passwords across systems: Importantly, FIM provides a simplified sign-on experience through its identity synchronization capabilities, delivering the ability to synchronize passwords across heterogeneous systems.
User Management
One of the most important things from a developer standpoint and business standpoint is automated, codeless, user provisioning. FIM delivers tools for integrated user management and self-service across enterprise applications without the costly coding of business rules or recoding of the target systems. These automated and centralized user management tools include:
- Declarative user provisioning: FIM provides a user interface to configure provisioning rather than requiring customized code to be written, as was the case in previous versions. Automated provisioning allows you to define, easily, the provisioning workflows associated with adding a new user to the enterprise and provisioning them with access to appropriate applications in an automated manner.
- Integrated provisioning of identities, credentials, and resources: Using management tools delivered in FIM, IT can create a policy to provision the appropriate accounts, resources, and credentials, associate to users, ensure the appropriate workflows are integrated into the process, and do this in a very seamless manner. This means that an enterprise can provide automated and integrated processes for new users when they come to the enterprise, which makes them more productive from day one. De-provisioning for users leaving the enterprise also becomes centralized and less complicated, which makes it easier to ensure complete de-provisioning and to handle future compliance audits.
- Self-service user profile management: New features in FIM make it possible for users to manage their own identity information. IT can use FIM to set policies to require workflows such as approvals for or notifications of these user-generated changes. For example, IT may choose to delegate management of mobile phone numbers to end users. Users would be able to use the FIM portal to update this information. This helps keep identity data such as mobile phone number up to date so that users can be easily contacted in the process of doing business.
Group Management
FIM provides powerful capabilities that help increase the productivity of end users, frees up IT from repetitive tasks and provide better security and compliance outcomes. These features include:
- Rich self-service group management tools: FIM provides self-service group and distribution list management with the FIM Web portal. Integration with Outlook enables end users to manage their group membership requests using the collaboration tools with which they are familiar, so as to provide maximum productivity with minimal additional training. For example, with approve and reject buttons functionality provided in Outlook for the purpose of providing approve or reject membership requests, FIM makes it possible for users to manage the membership of groups without requiring the assistance of the IT organization. FIM end users can create distribution lists for new virtual teams and manage requests made by others to join a distribution list.
- Offline approvals through Outlook: Capabilities to manage group membership are in FIM integrated into Outlook. This enables users to use Outlook to, as an example, request membership in a group or manage approvals while they are offline.
- 6. Automated group and distribution list updates: In addition to the self-service management of group membership, FIM also supports the dynamic calculation of group members based on the characteristics of any resource(s). With this feature, users are added and removed from groups automatically. For example, IT can configure a group designed to control access to the resources of a team so that only the manager and the direct reports are members. In this case, FIM can calculate the group membership based on the manager attribute of the user resource. In case of structural changes to the team, such as members joining or leaving the team, the group membership is automatically updated. Dynamic group membership helps reduce the manual interaction required to protect, effectively, resources.